When we talk about cybersecurity for saas, we're not just talking about tech. It's a core business function, all about protecting your data, your users, and your settings inside an environment you don't fully control. Think of it as a proactive game plan for managing risk on platforms that have become the very backbone of how we work. It’s what ensures your operations keep running and your customers keep trusting you.
Why SaaS Cybersecurity is No Longer Optional

As more businesses move their critical operations from CRMs to data analytics to cloud-based apps, the potential attack surface has exploded. This shift has completely torn down the old-school security perimeter, making robust cybersecurity for SaaS an absolute necessity, not just a nice-to-have. The fallout from a breach, including data loss, steep fines, and a trashed reputation, is simply too great to risk.
To really get it, you need to understand the shared responsibility model. It's a fundamental concept in the cloud world. Imagine your SaaS provider is the landlord of a high-security apartment building. They’re on the hook for the building’s foundation, the security at the main entrance, and the overall structural integrity. They keep the building itself safe.
But as the tenant, you are entirely responsible for what happens inside your own unit. You have to lock your door, decide who gets a key, and safeguard your valuables. In the SaaS world, this translates to the vendor securing the underlying infrastructure, while you handle:
Managing user access and identities to make sure only the right people get in.
Configuring application security settings to match your company's own security policies.
Protecting the data you and your customers store within the application.
Staying compliant with all relevant industry and government regulations.
The Core Challenges Ahead
Getting a handle on this division of labour is the first step. The real trick is navigating the challenges that come with it. The fierce competition between software providers means new features are often pushed out at lightning speed, sometimes with security taking a back seat. This often leaves you, the customer, to sort out a maze of complex security configurations on your own.
This guide is your roadmap for securing your SaaS ecosystem. We're cutting through the technical jargon to get to the heart of what businesses need: protecting assets, managing identities, and meeting tough compliance standards in a world that never stands still.
We'll walk you through the essential strategies for building a truly resilient security posture. From spotting modern threats to designing a solid security architecture and responding effectively when things go wrong, our goal is to give you the knowledge you need. We want to help you turn security from a reactive chore into a strategic advantage, a core principle behind all of our Cyber Security Services.
Decoding the Modern SaaS Threat Landscape
To really get a handle on defending your SaaS environment, you first need to get inside an attacker's head. Forget the old-school image of hackers hammering away at your firewalls. Today's game is far more subtle. It's about finding the weakest link in the chain, which almost always turns out to be user identity. This reality forces us to think differently about security. The user's login is now the front door to your most critical data.
Think of your identity provider (IdP), whether it's Google Workspace or Microsoft Entra ID, as your company's digital passport office. It's the central authority issuing the credentials that unlock access to dozens, if not hundreds, of connected applications. If an attacker compromises that hub, they don't just steal one key. They get the master key to your entire digital kingdom. It's no surprise that this is the primary entry point for most SaaS breaches we see today.
The explosion of SaaS tools has, predictably, brought a surge in related security incidents. A recent SaaS Security Threat Report uncovered a massive 300% year-over-year jump in SaaS breaches. But here’s the kicker: the report found that a jaw-dropping 99% of these compromises began at the identity provider. That single statistic tells you everything you need to know about where your focus should be.
Common Attack Vectors Targeting SaaS Identity
Attackers have become incredibly skilled at sidestepping defences we once thought were foolproof, like multi-factor authentication (MFA). Knowing their playbook is the first step to building a defence that actually works.
MFA Fatigue Attacks: This is a brute-force attack on human patience. An attacker gets a password and then just spams the user's phone with push notifications, betting that they'll eventually hit "approve" just to make the noise stop. And it works.
Session Hijacking: Why bother with passwords or MFA when you can just steal an active session? Attackers grab a user's session cookie from their browser, which lets them waltz right into an application, completely impersonating the legitimate user.
Malicious OAuth Consent: We've all seen those "Log in with Google" buttons. Attackers create malicious third-party apps and trick users into granting them permissions to their accounts. Once approved, the app quietly siphons data in the background, often going completely unnoticed.
These identity-first attacks signal a major shift in how adversaries think. As we covered in our guide on emerging cybersecurity trends for digital threats, attackers are now laser-focused on the human element and the tangled web of trust between cloud services.
The Silent Dangers Lurking Within
Beyond direct attacks, a handful of internal vulnerabilities can create the perfect storm for a breach. These aren't usually the result of malicious intent, but rather a slow drip of oversights and neglected hygiene that builds up into a massive risk.
The biggest SaaS security threats often don't come from sophisticated hackers in dark rooms. They come from the slow creep of misconfigurations, excessive permissions, and rogue apps that go completely unnoticed until it's too late.
One of the most common culprits is over-privileged users. Does someone in marketing really need admin rights to your finance platform? Probably not. Yet, for the sake of convenience, permissions are often handed out like candy and never reviewed, creating a huge blast radius if that one account gets compromised.
Another silent killer is misconfigured settings. Your average SaaS app has hundreds of security toggles. A single wrong flip of a switch, like allowing public file sharing by default or turning off a crucial audit log, can expose your entire organisation. These settings are complex, and vendors often default to less secure options to make the user experience smoother out of the box.
Finally, there's the persistent headache of Shadow IT. This is what happens when employees sign up for and use SaaS apps without anyone in IT knowing about it. These unsanctioned tools are a complete blind spot. They aren't vetted, they probably have weak access controls, and they create a shadow repository of company data that you can't govern or protect. Getting a grip on these internal issues is absolutely fundamental to any effective cybersecurity strategy.
How to Build a Resilient SaaS Security Architecture
Once you’ve mapped out the threats, the next logical step is to build a solid defence. A resilient security architecture isn't something you can just buy off the shelf; it's a deliberate, multi-layered strategy designed to protect your data from every possible angle.
The best way to picture this is like constructing a secure building. Each component from the foundation to the locks on the doors serves a specific protective purpose. This layered approach, often called "defence-in-depth," is fundamental to our own Cyber Security and Compliance Services. It means that if one layer fails, another is already in place to stop an intruder dead in their tracks.
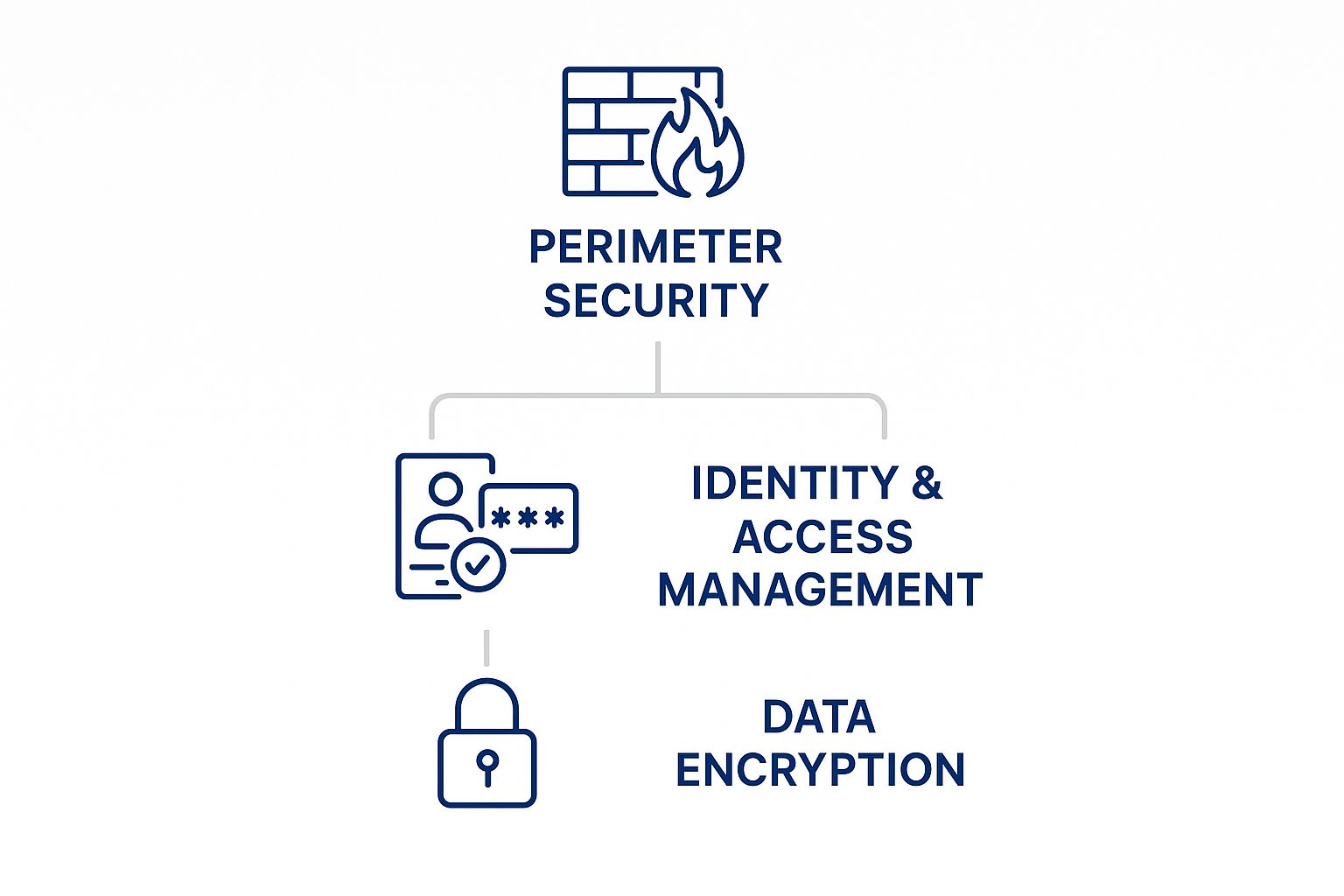
The diagram above gives you a sense of how different security controls, from perimeter defences to data-level encryption, stack together to create a formidable barrier. This strategy is the bedrock of modern cybersecurity for SaaS and ensures you're not leaving any doors unlocked.
The Foundation: Your Identity and Access Management
Every solid structure starts with a strong foundation. In the world of SaaS security, that foundation is Identity and Access Management (IAM). In an age where the traditional network perimeter has all but disappeared, identity is the new perimeter.
Controlling who can access your systems and what they can actually do once they're inside is the most critical part of your entire security program. If your IAM foundation is shaky, every other security measure you put in place becomes that much weaker.
The cornerstone here is the principle of least privilege. It's a simple but powerful idea: users should only have the absolute minimum level of access needed to do their jobs. Nothing more. An accountant doesn't need admin rights to your marketing platform, and a sales rep has no business poking around in the finance software.
To make this a reality, you need to take two key actions:
Strict Role-Based Access Control (RBAC): Define roles with specific, granular permissions and assign users to them. Get rid of those generic "user" roles that grant overly broad access.
Regular Access Reviews: At least once a quarter, you need to review who has access to what. This routine helps you catch and revoke unnecessary permissions that tend to build up over time, a problem often called "privilege creep."
Of course, permissions don't mean much if an attacker can just steal a user's credentials. This is why strong multi-factor authentication (MFA) is completely non-negotiable. Think of MFA as the reinforced steel in your foundation; it makes it exponentially harder for an intruder to get in, even if they've managed to get their hands on a valid password.
The Walls: Your Data Protection Measures
With a solid foundation laid, it's time to build the walls that protect your most valuable assets: your data. A smart data protection strategy boils down to understanding what data you have, where it lives, and how to shield it from prying eyes, whether it's sitting on a server or moving across a network.
The first step is data classification. Let's be honest, not all data is created equal. You need to categorise your information based on how sensitive it is; for example, public, internal, confidential, and restricted. This allows you to apply the right level of security to the right data.
It's a bit like a bank vault. You wouldn't store office supplies in the same high-security safe as your most critical corporate secrets. Data classification applies that exact same logic to your digital assets, ensuring your most sensitive information gets the strongest possible protection.
Once your data is classified, encryption becomes your primary shield. All data should be encrypted both in transit (as it travels over networks) and at rest (when it's stored on servers or in databases). This ensures that even if an attacker manages to intercept or steal the data, it remains a scrambled, useless mess without the decryption key.
For a deeper dive into these foundational security ideas, you might find some of our other resources on software security best practices helpful.
The Security System: Your Continuous Monitoring
Finally, every secure building needs a state-of-the-art alarm system. In SaaS security, this is your continuous monitoring and configuration management program. SaaS applications are incredibly dynamic; settings, integrations, and user permissions are constantly changing. Without a watchful eye, your carefully built defences can start to degrade surprisingly quickly.
This is where tools for SaaS Security Posture Management (SSPM) come into play. These platforms act as your digital security guards, constantly scanning your SaaS environments for misconfigurations, compliance violations, and risky permissions. They give you a single, centralised dashboard to spot and fix flaws before they can be exploited, turning security from a one-time project into an ongoing, automated process.
Mastering Identity as Your New Security Perimeter

The days of relying on a strong firewall to keep the bad guys out are long gone. In the world of SaaS, your company's data isn't tucked away neatly on-premise; it's spread across a vast ecosystem of cloud apps. This means the old castle-and-moat security model is officially broken.
Your new perimeter is the digital identity of every single user, application, and device that touches your data. Getting this right is the absolute cornerstone of a modern SaaS cybersecurity strategy.
This isn't just about ticking the multi-factor authentication (MFA) box and moving on. Attackers are constantly upping their game, finding clever ways to sidestep weak MFA setups through social engineering and technical exploits. A deep understanding of Two-Factor Authentication (2FA) is the first, crucial step toward building a defence that can actually withstand a real-world attack.
And it’s not just human users we need to worry about. The whole SaaS model runs on non-human identities like API keys and service accounts, which let different applications talk to one another. These connections often have broad, always-on permissions, making them a goldmine for attackers looking for a direct route to your most sensitive systems.
The Hidden Risks of an Interconnected Ecosystem
One of the sneakiest threats we see comes from the countless integrations we all use. Every time an employee connects a third-party app or a new AI tool to a core system like Microsoft 365 or Google Workspace, they're potentially opening a new door for attackers. These apps frequently ask for sweeping permissions that go far beyond what they actually need to function.
The numbers paint a pretty stark picture. One recent report found that a shocking 46% of SaaS breaches were tied to weak or compromised MFA. On top of that, 56% of companies admitted to having overprivileged API access to sensitive data through third-party vendors and AI tools, while 58% struggled to enforce the right privilege levels.
What these statistics show is a massive blind spot. Without a central way to see and manage all these connections, your organisation is wide open to a breach coming from a vendor you barely remember approving. It’s a huge vulnerability that can be easily overlooked.
Establishing a Centralised Identity Provider
To get a handle on this chaos, a centralised identity provider (IdP) is an absolute must-have. Think of tools like Microsoft Entra ID or Okta as a single source of truth for all your user identities and access rules. It’s the command centre you need to apply consistent security policies across every single app you use.
By funnelling all authentication requests through a single, hardened IdP, you eliminate inconsistent security policies and gain the visibility needed to detect and respond to threats effectively. It transforms identity management from a chaotic, app-by-app chore into a coherent, strategic defence.
A centralised IdP lets you enforce critical security measures across the board:
Adaptive MFA: Instead of basic MFA, you can implement smarter policies that demand stronger proof of identity based on risk signals like an unusual location, a new device, or odd login times.
Consistent Policy Enforcement: You can ensure that password rules, access policies, and session timeouts are identical for every application, closing dangerous security gaps.
Simplified Access Reviews: Auditing who has access to what becomes much simpler. You can run regular, effective reviews from one dashboard to make sure people only have the permissions they truly need for their job.
The security of these application-to-application connections is just as important. Protecting the pathways that non-human identities use is a specialized skill. For a deeper dive into that, check out our guide on API security testing: https://www.cleffex.com/blog/api-security-testing/
Before we wrap up, let's look at the core components of a strong identity and access management program in a SaaS environment.
Key Pillars of SaaS Identity and Access Management
This table summarises the core components and best practices for securing both user and non-human identities in your SaaS setup.
Pillar | Objective | Key Actions |
|---|---|---|
Centralised Identity (IdP) | Establish a single source of truth for all identities and enforce consistent security policies. | Implement an IdP like Microsoft Entra ID or Okta; integrate all SaaS apps for Single Sign-On (SSO). |
Strong Authentication | Protect against credential theft and unauthorised access by verifying user identities. | Enforce phishing-resistant MFA across all applications; implement adaptive policies based on risk signals. |
Principle of Least Privilege | Ensure users and applications only have the minimum access required to perform their functions. | Conduct regular access reviews; automate de-provisioning; use Just-in-Time (JIT) access for sensitive systems. |
Non-Human Identity Management | Secure API keys, service accounts, and other automated identities to prevent misuse. | Discover and inventory all non-human identities; rotate secrets regularly; monitor API traffic for anomalies. |
Third-Party App Governance | Control and monitor the permissions granted to third-party applications integrated with your core systems. | Vet all new integrations; review OAuth grants and permissions; remove unused or overprivileged apps. |
Securing the identity perimeter isn't a one-and-done project; it's an ongoing discipline. But out of all the investments you can make in your SaaS security, this is the one that will give you the most significant and lasting protection.
Here is the rewritten section, designed to sound completely human-written and natural.
Sailing the Seas of SaaS Compliance
Great security is about more than just repelling attacks; it’s about proving to your customers and regulators that you're a trustworthy guardian of their data. That's where compliance enters the picture. It takes your security efforts from a list of technical controls and turns them into a verifiable framework that builds confidence and opens doors for your business.
At first glance, compliance can feel like a tangled mess of acronyms and legalese. But if you strip all that away, the core idea is simple. It's about making sure your security practices line up with established industry standards and regulations. Think of it as a universal language for security. The one that lets you clearly communicate just how seriously you take protecting sensitive information.
For any business building in the cloud, getting a handle on compliance isn't just a "nice-to-have." It’s an essential part of delivering reliable cybersecurity for SaaS. Whether you're trying to win over big enterprise clients or break into new global markets, a solid compliance posture is your non-negotiable ticket to play.
Breaking Down the Big Compliance Frameworks
While there are dozens of regulations out there, a handful of key frameworks really form the bedrock of most SaaS compliance strategies. Each has a slightly different focus, but you’ll find they often share a lot of the same underlying security controls.
SOC 2 (Service Organization Control 2): This is the heavyweight champion for SaaS companies, especially in North America. It’s built around five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. A clean SOC 2 report is basically an auditor giving you a stamp of approval, confirming you have the right systems in place to keep customer data safe.
ISO 27001: This is the go-to international standard for managing information security. It gives you a complete playbook for setting up, running, and constantly improving an Information Security Management System (ISMS). For companies looking to do business on a global scale, ISO 27001 certification is often a must.
GDPR (General Data Protection Regulation): This landmark EU regulation completely changed the game for data privacy. It dictates how companies are allowed to collect, use, and store the personal data of anyone in the EU. With hefty fines for getting it wrong, GDPR set a new global standard that everyone has to pay attention to.
You shouldn't treat compliance like a separate, bureaucratic chore you have to check off a list. The smartest approach is to see it as the natural result of a well-built security program, where the good work you're already doing maps directly to what regulators want to see.
This philosophy is at the heart of our Cyber Security and Compliance Services. We focus on helping businesses build security in a way that makes compliance feel like a seamless part of the process, not a painful afterthought.
Moving from Checkboxes to Continuous Readiness
Getting a certification is a huge milestone, but it’s definitely not the finish line. The real objective is to achieve continuous readiness, a state where your organization is always operating in a compliant way. In the fast-moving world of SaaS, shifting from frantic, once-a-year audits to this kind of ongoing vigilance is absolutely critical.
Automation is your best friend here. Modern tools can constantly scan your cloud setup, flag any drifts from your compliance baseline, and gather the necessary evidence on autopilot. This doesn't just cut down on the soul-crushing manual work of preparing for an audit; it gives you real-time confidence that your security controls are actually working day in and day out. As SaaS providers work through the compliance puzzle, establishing foundational legal documents like a robust privacy policy is a key step in showing a commitment to data protection and building user trust.
Ultimately, navigating compliance is about creating a culture of security that permeates every corner of your organization. As we build out a full suite of Cyber Security Services, we see time and again that the companies that get this right don't just reduce their risk, but they gain a serious competitive edge. For a broader look at integrating new security measures, consider the principles we covered in our cybersecurity adoption guide. This foundational knowledge is reinforced by the expertise our team brings, which you can learn more about on our about us page.
Your Playbook for SaaS Incident Response
Let's be realistic: even with the best defences in place, incidents happen. In the world of SaaS cybersecurity, it’s not a matter of if, but when. A prepared organization is a resilient one, and that means having a clear, actionable incident response (IR) playbook is non-negotiable. This isn’t about scrambling in a panic; it's about having a calm, methodical process ready to go, designed to minimize damage and get you back to business quickly.
The biggest hurdle in a SaaS incident? It's almost always a lack of visibility. When your user activity is scattered across dozens of different applications, trying to spot a genuine threat can feel like finding a needle in a haystack. This is exactly why the first step in any solid IR strategy is to centralize your logs. Pulling the audit logs from all your critical SaaS apps into a single security information and event management (SIEM) tool gives you that unified view you absolutely need for any meaningful analysis.
A Step-by-Step Incident Response Workflow
When an alert goes off, your team can't make it up as they go. A well-defined workflow ensures that critical steps aren't missed in the heat of the moment.
Detection and Analysis: This is the initial "what's going on?" phase. Your security team jumps on the alert, digging into those centralized logs to connect the dots across different platforms. The goal is to figure out fast if it's a false positive or a legitimate threat and to get a sense of its potential scope.
Containment: Once you've confirmed a threat, the immediate priority is to stop the bleeding. This could mean disabling a compromised user account, revoking an abused API key, or blocking a malicious IP address. The key is to isolate the attacker and cut off their ability to move deeper into your environment.
Eradication and Recovery: With the immediate danger contained, the focus shifts to kicking the attacker out for good. This means finding and patching the root vulnerability they used to get in. After that, recovery involves carefully restoring systems and data from clean backups, making absolutely sure the environment is secure before you bring it back online.
Bridging the Confidence and Risk Gap
Recent data paints a pretty worrying picture. A survey found that a staggering 75% of organizations dealt with a SaaS security incident in the last year, which is a sharp 33% jump from the year before. Here's the kicker: despite this, 91% of them said they had high confidence in their security. That reveals a massive gap between perceived safety and actual risk. You can dig into more of these findings on appomni.com.
This mismatch really highlights why a tested incident response plan is so critical that it moves you from just assuming you're ready to knowing you are.
An incident response plan isn't a document that gathers dust on a shelf. It's a living playbook. You need to test it regularly with tabletop exercises and fire drills. This is what builds muscle memory, ensuring your team can execute flawlessly when it really counts.
Building this kind of real-world readiness is a cornerstone of our comprehensive Cyber Security and Compliance Services. It reinforces the expertise and trust we talk about on our About Us page, showing our commitment to not just prevention, but to rapid and effective recovery as well.
Frequently Asked Questions About SaaS Cybersecurity

When you're dealing with the nitty-gritty of cybersecurity for SaaS, a lot of practical questions tend to pop up. Let's tackle some of the most common ones with clear, straightforward answers to help you put these concepts into practice.
Who is Responsible for Security in a SaaS Model?
It's a team effort, really. SaaS security is built on what's known as a shared responsibility model.
The SaaS provider takes care of securing their end of the bargain, the infrastructure, the network, and the application itself. Think of this as "security of the cloud."
But you, the customer, are on the hook for securing what happens inside that application. This means managing who has access, setting up security configurations correctly, and keeping an eye on user activity. This is "security in the cloud," and knowing where that line is drawn is absolutely essential.
What is the Biggest Security Risk for SaaS Applications?
If you ask any security professional, they'll likely give you the same answer: identity-based attacks. Threat reports consistently show this is the single biggest risk factor. We're talking about everything from stolen passwords and poorly implemented multi-factor authentication (MFA) to insiders misusing high-level access.
Because SaaS apps are designed to be accessed from anywhere, a compromised user account is a direct key to your sensitive data. This is why a rock-solid Identity and Access Management (IAM) program isn't just a nice-to-have; it's the cornerstone of any effective SaaS security plan.
How Can I Assess a New SaaS Vendor?
Vetting a new vendor properly comes down to doing your homework. You need to kick the tyres, and that starts by asking for their key security documents. Look for things like SOC 2 Type II reports or ISO 27001 certifications, which are independent audits that verify their security controls are actually working.
A vendor's transparency about their security is a huge tell. If they're open and willing to share reports and answer tough questions, it's a great sign. If they get defensive or vague, that’s a major red flag.
Dig into their policies on data encryption, how they handle incident response, and what they do with your data when you leave. You also need to get crystal clear on their specific shared responsibility model, so you know exactly which security tasks are yours to manage. As we explored in our cybersecurity adoption guide, this level of scrutiny is non-negotiable for bringing new tools into your environment safely.
What Is SaaS Security Posture Management?
SaaS Security Posture Management (SSPM) refers to a category of automated tools that give you a bird's-eye view of the security risks across all your SaaS applications. These platforms constantly scan your environments, such as Microsoft 365 or Salesforce, for potential problems.
SSPM tools hunt for common security gaps like misconfigurations, compliance violations, or users with far more permissions than they need. They pull all this information into a single dashboard, giving security teams a fighting chance to manage the sprawl of a modern SaaS ecosystem. Many even help automatically fix the issues they find. This kind of oversight is a core part of our Cyber Security and Compliance Services. You can learn more about our team’s deep expertise in this area on our about us page.
At Cleffex Digital Ltd, our job is to turn complex security problems into clear, practical strategies. Our Cyber Security Services are built to help you create a resilient and compliant SaaS environment that stands up to modern threats.







