Cyber security isn't just an IT problem anymore. It's a core part of keeping your business alive and growing. At its heart, it's about protecting all your company's digital assets, from sensitive customer data to internal financial records, against theft, damage, or prying eyes. Not taking it seriously is like leaving the front door of your shop unlocked overnight.
Why Cyber Security is a Core Business Function

Many business owners fall into the trap of thinking, "We're too small to be a target." The reality is quite different. Recent reports show that small businesses are the target of a staggering 43% of cyber attacks. Attackers often see smaller companies as low-hanging fruit precisely because they tend to have fewer security measures in place.
Think of your business's digital footprint as its new storefront. Your website, customer database, and internal communications are all valuable assets. Without proper protection, you're essentially leaving doors and windows wide open for criminals to walk right in. The fallout from a breach is far more than just a technical headache.
The True Business Impact of a Cyber Attack
The damage from a cyber incident hits your bottom line and your reputation hard. It's not just about the data you lose; it’s about the trust you lose and the operational chaos that follows. The real-world consequences are serious:
Financial Loss: The direct costs can be crippling. Think remediation services, regulatory fines, and even ransom payments. Many small businesses simply can't absorb the financial shock of a major breach and never fully recover.
Reputational Damage: Your customers give you their personal information because they trust you. A breach shatters that trust, and winning it back is an uphill battle.
Operational Disruption: Imagine your entire operation grinding to a halt. A ransomware attack can lock you out of your systems for days or weeks, making it impossible to serve customers, process payments, or even access your own files.
Legal and Regulatory Penalties: Data protection laws come with heavy penalties for non-compliance. If you do business in the EU or handle data from EU citizens, regulations like GDPR are non-negotiable. Following a clear GDPR compliance checklist is essential to avoid these fines.
A cyber attack involves immediate financial impacts like business interruption and legal fees, but it also leads to longer-term damage, including harm to brand reputation and lost trust from customers and employees.
Shifting from Cost to Investment
Treating cyber security as just another expense is one of the biggest mistakes a business can make. It's an investment in your company's stability and future. You wouldn't think twice about insuring your physical office or equipment, and your digital assets deserve the same level of protection.
A proactive approach to security does more than just prevent disasters. It builds a foundation for growth and stability. When clients, partners, and your own team know you take security seriously, it shows you're a responsible and trustworthy organization. That strengthens your brand and solidifies your position in the market for the long haul.
Understanding Today's Most Common Cyber Threats

Before you can build a solid defence, you need a clear picture of what you're up against. Cyber threats aren't just abstract concepts; they are real-world tools and tactics criminals use to steal money, snatch data, or simply cause chaos. Often, these attacks hinge on simple human error, making awareness the very first line of defence.
Think of these threats as different ways a burglar might try to get into your office. One might try to pick the lock, another might trick an employee into handing over the keys, and a third might hold your entire operation hostage. Knowing their methods is the only way to stay a step ahead.
Phishing: The Art Of Deception
Phishing is easily one of the most common and damaging attack methods out there. At its heart, it's a social engineering con where an attacker pretends to be someone you trust, like a bank, a key supplier, or even your company's CEO in an email or message.
Imagine getting an email that looks exactly like it's from your main shipping partner, complete with the right logo and colours. It warns you about a "delayed package" and provides a link to track it. But that link leads to a convincing fake login page designed to steal your password. It's the digital equivalent of a scam artist in a perfect uniform asking for your keys.
Phishing isn’t just an email problem anymore. Attackers now regularly use text messages (smishing) and social media DMs, opening up even more ways to reach your team.
The ultimate goal is to trick someone into giving up sensitive information, like passwords, credit card details, or proprietary business data. Once they have that, attackers can waltz right into your accounts, move money, or plant even more dangerous malware.
Ransomware: The Digital Hostage Crisis
Ransomware is a particularly nasty type of malware that locks up your files by encrypting them, making everything completely inaccessible. The attackers then demand a ransom – usually in cryptocurrency – for the decryption key that will, in theory, restore your access.
For a business, a ransomware attack is a full-stop operational shutdown. It's like a thief breaking in, changing the locks on every door, filing cabinet, and computer, and then leaving a note demanding a hefty payment for the new keys. In the meantime, you can't access customer records, process orders, or even run payroll.
The damage goes far beyond the ransom demand itself. Downtime can cost a business thousands of dollars an hour, and even if you pay up, there's no guarantee the attackers will actually provide a working decryption key. This is precisely why rock-solid data backups are non-negotiable for any business serious about cyber security. To get a better handle on what's out there, it helps to review the Top 10 Cybersecurity Threats currently making the rounds.
Malware: The Unwanted Intruder
Malware, which is short for "malicious software," is a catch-all term for viruses, spyware, trojans, and any other program built to cause harm. It can sneak onto your systems through infected email attachments, shady downloads, or by exploiting unpatched software vulnerabilities.
Once it's inside your network, different types of malware get to work in different ways:
Spyware: Quietly collects information about you or your organisation and sends it back to the attacker.
Viruses: Latch onto clean files and spread from one computer to another, often corrupting data or crashing systems along the way.
Trojans: Disguise themselves as legitimate software to fool you into installing them, creating a hidden backdoor for attackers to come and go as they please.
Keeping up with new dangers is a constant battle. The threat landscape is always shifting, and you can get a deeper understanding of what’s on the horizon by exploring the latest cybersecurity trends for digital threats.
Common Cyber Threats and Their Business Impact
To put it all into perspective, here's a quick look at the most common threats and the specific damage they can inflict on a business.
Threat Type | How It Works (Simplified) | Primary Business Impact |
|---|---|---|
Phishing | Tricking employees into revealing sensitive info (e.g., passwords, financial details) via deceptive emails or messages. | Data breaches, financial fraud, unauthorized access to critical systems, and reputational damage. |
Ransomware | Encrypting company data and demanding a ransom payment for its release effectively halts operations. | Complete business shutdown, significant financial loss (downtime & ransom), permanent data loss. |
Malware | Installing harmful software (viruses, spyware) to steal data, disrupt systems, or gain control of the network. | Data theft, operational disruption, system crashes, and compromised intellectual property. |
Insider Threats | Current or former employees intentionally or unintentionally misuse their authorized access to compromise data. | Data leakage, sabotage of internal systems, financial fraud, loss of customer trust. |
Denial-of-Service (DoS) | Overwhelming a website or server with traffic to make it unavailable to legitimate users. | Website and service unavailability, lost revenue, and damage to brand reputation. |
Understanding these attack vectors is the foundational first step. When you know how these threats work and what they're targeting, you can start building a much smarter, more effective defence for your entire organisation.
Building Your Multi-Layered Defence Strategy
In today's threat-filled digital world, relying on a single security tool is like putting one lock on a bank vault. It’s simply not enough. The most effective approach to cyber security for business is what we call “defence in depth.” The core idea is to build multiple, overlapping layers of security. If one layer fails, others are ready to catch the threat.
Think of it like securing a medieval castle. A castle doesn't just have one big wall. It has a wide moat, towering outer walls, vigilant guards, and a heavily fortified inner keep for the real treasures. If an intruder somehow gets past one obstacle, they’re immediately confronted by another.
Your company's digital assets deserve that same robust, layered protection. Each layer is designed to address a different type of vulnerability, creating a security posture that is tough, resilient, and ready for anything.
The Moat and Walls: Your Digital Access Control
The first and most fundamental layers of your defence are all about keeping unauthorized people out of your network in the first place. This is your digital perimeter; the moat and walls of your castle.
Firewalls: This is your moat. A firewall acts as a critical filter between your private, internal network and the wild west of the internet. It inspects all incoming and outgoing traffic, blocking anything malicious before it even gets a chance to touch your systems based on a predefined set of security rules.
Access Controls: These are your walls and gates. Let's be realistic: not every employee needs the keys to the entire kingdom. By implementing the principle of least privilege, you ensure that people only have access to the specific information and tools they absolutely need to do their jobs.
This one measure dramatically shrinks your potential attack surface. If an employee's account is ever compromised, the damage is contained to whatever that single account could access, not your entire network.
The Guards: Your Trained and Aware Employees
Your employees are the guards patrolling the castle walls. A well-trained guard can spot an enemy impersonator a mile off, but an untrained one might be tricked into lowering the drawbridge. Human error is still one of the biggest factors in security breaches, which makes ongoing employee training an essential layer of your defence.
A solid security awareness program can turn your team from a potential weak link into your greatest security asset. This means continuous education on spotting threats like phishing emails, handling sensitive data properly, and understanding the vital importance of using strong, unique passwords.
This infographic shows just how direct the impact of investing in employee training and awareness can be.
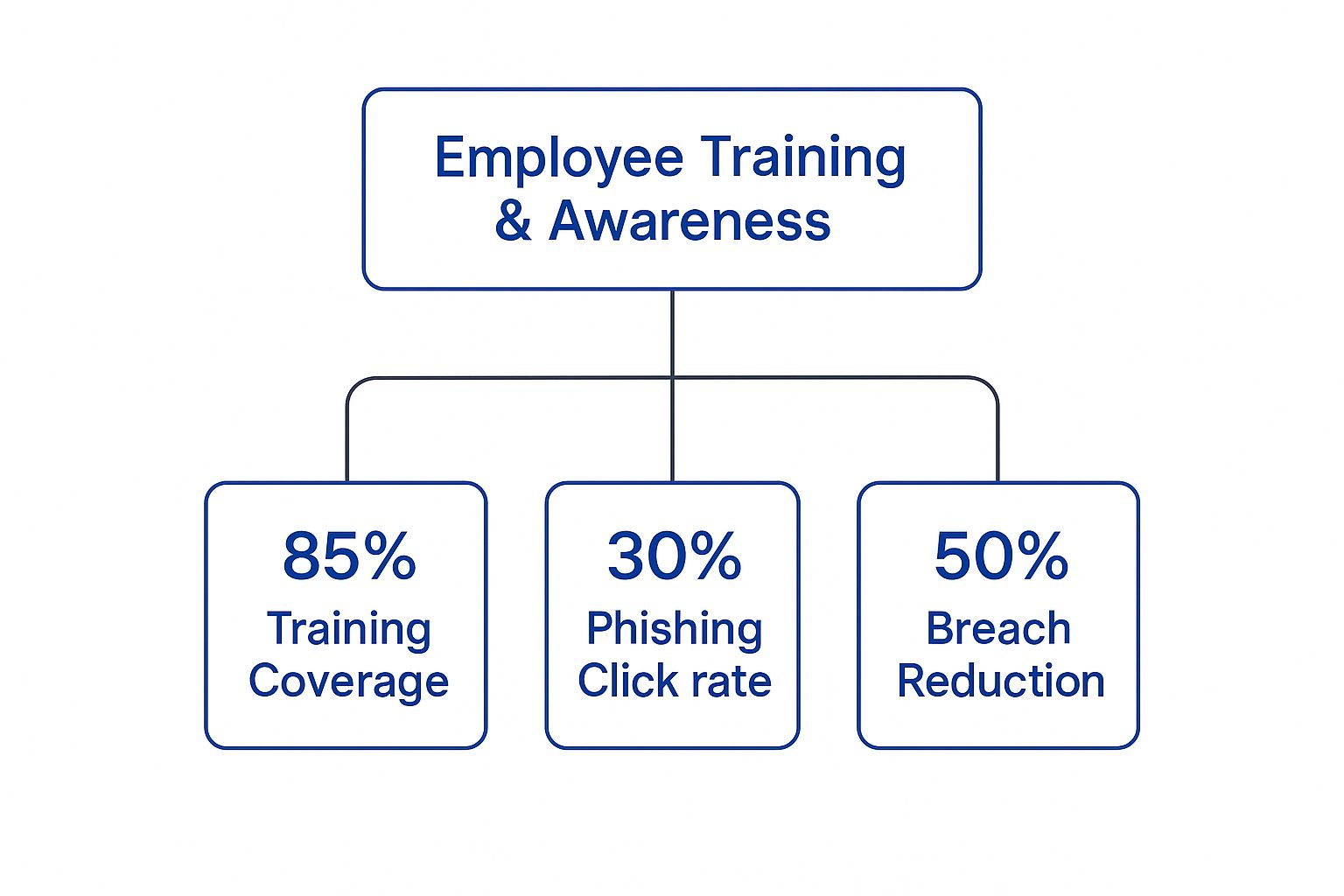
As you can see, comprehensive training doesn't just lower phishing susceptibility; it can lead to a massive reduction in actual security breaches.
The Secure Keep: Protecting Your Core Data
Finally, at the very centre of your castle is the keep, the last line of defence where your most critical assets are stored. For your business, this is your sensitive data: customer lists, financial records, and priceless intellectual property.
Data Encryption: Think of encryption as locking your treasures in a vault that can only be opened with a unique, complex key. Even if a thief manages to get inside the keep and steal the box, the contents are completely useless to them. Encrypting data both "at rest" (when it's sitting on a server) and "in transit" (when it's being sent over the internet) is non-negotiable.
Multi-Factor Authentication (MFA): This is like requiring a secret handshake on top of the key to get into the keep. MFA adds a powerful layer of verification by asking users for two or more credentials to log in, usually a password plus a one-time code sent to their phone. This makes it exponentially harder for an attacker to get in, even if they somehow manage to steal a password.
Bringing It All Together With an Incident Response Plan
A truly complete defence strategy must also account for the worst-case scenario: what do you do when an attack actually succeeds? An Incident Response Plan (IRP) is your castle's emergency protocol. It outlines the precise steps your team will take to contain a breach, eradicate the threat, and recover as quickly as possible, minimizing both downtime and damage.
Implementing these layers doesn't have to be a monumental task. The goal is to build a security framework that is powerful but also adaptable to your specific business needs. A great place to start is by ensuring your online platforms are built securely from day one by following established web application security best practices.
The Human Element: Your First Line of Defence

While we put a lot of faith in firewalls and encryption, they only tell part of the story when it comes to cyber security for business. The most sophisticated technology can be completely bypassed by a single, accidental click. At the end of the day, your employees are the gatekeepers to your entire digital kingdom, facing down potential threats in every email, download, and website they visit.
Technology alone can never be a complete solution because it doesn't account for human curiosity or a simple moment of distraction. Attackers understand this perfectly, which is why so many modern cyber attacks are designed to manipulate people, not just breach software.
This makes your team the most critical variable in your security equation. Without proper training, they can be your biggest vulnerability. But armed with the right knowledge and tools, they become your most powerful and vigilant security asset.
Building a Security-First Culture
A truly strong security posture starts with your company culture, not your code. A "security-first" culture is an environment where every single person, from the CEO down to the newest hire, understands their personal role in protecting the company. It's about fundamentally shifting the mindset from "security is IT's job" to "security is everyone's job."
This kind of shift doesn't happen by forcing everyone to sit through a dull, once-a-year slideshow presentation. It requires ongoing, engaging education that builds real-world awareness and gives employees the confidence to act when something seems wrong.
Empowering your team with knowledge and making them feel like active partners in your defence strategy is far more effective than just imposing rules. An informed employee is a formidable line of defence.
When this culture takes root, good security practices become a natural reflex. It’s the employee who instinctively pauses before clicking a suspicious link, the manager who picks up the phone to verify a strange payment request, and the team member who isn't afraid to report something that just feels "off."
Practical Training That Actually Works
Effective training needs to move beyond theory and get hands-on. The goal is to build muscle memory for spotting and responding to threats, so your team reacts correctly when it really counts.
Here are a few strategies that deliver tangible results:
Simulated Phishing Campaigns: One of the best ways to teach is to do. Regularly sending your own fake phishing emails to staff provides a safe way to experience a real attack scenario. It's a powerful tool for gauging awareness and creates an immediate, teachable moment for anyone who clicks.
Micro-Learning Modules: Ditch the long, draining seminars. Instead, use short, focused videos or interactive quizzes on specific topics, like how to create strong passwords or recognise ransomware warnings. This approach respects people's time, keeps them engaged, and makes the information much easier to remember.
Clear Reporting Protocols: Make it incredibly easy for employees to report something suspicious. A one-click "report phish" button in your email program or a dedicated, no-blame channel for security questions encourages people to speak up without fear of getting in trouble.
Ultimately, turning your staff into a defensive force is about empowerment. When people understand the "why" behind security policies and feel equipped to contribute, they become an active, essential part of your multi-layered defence. This human firewall is often what stops a major breach before it ever gets started.
Choosing the Right Tools to Stay Ahead of Threats
Having a solid defence strategy and a security-aware team are the cornerstones of business cyber security. But to truly get ahead of attackers, you need to stop just reacting and start being proactive. It's all about actively hunting for weaknesses in your own systems before a criminal does.
Modern security isn’t just about building walls anymore; it’s about constantly checking those walls for cracks and reinforcing them. Adopting proactive technologies gives you the power to anticipate threats, find vulnerabilities, and shut them down before they can be exploited. This shifts your entire security approach from a frantic scramble to a forward-thinking strategy.
Making smart investments in the right technology is what makes this shift possible. The goal is to pick tools that align with your specific business risks, helping you systematically identify and fix security gaps.
Finding Weaknesses Before Attackers Do
The best way to stop an intruder is to think like one. Two critical practices, vulnerability scanning and penetration testing, let you do just that. They essentially simulate an attack on your own infrastructure to uncover any exploitable flaws.
Vulnerability Scanning: Think of this as an automated security patrol. These tools regularly sweep your networks, servers, and applications, looking for known vulnerabilities like outdated software or misconfigured firewalls. They generate a report that hands your IT team a clear to-do list for patching the most critical security holes.
Penetration Testing (Pentesting): This takes things to the next level. A penetration test is like hiring a team of ethical hackers to try and break into your digital fortress. They use the same creative techniques as real-world attackers to find and exploit weaknesses, giving you an invaluable, hands-on assessment of your defences.
A penetration test doesn't just point out theoretical problems; it proves how those issues could be used to cause real business damage. This kind of hard evidence is exactly what you need to prioritize security fixes and justify the investment.
Essential Tools for a Modern Defence
Beyond finding vulnerabilities, you need tools that actively monitor and protect your business operations day in and day out. A few key technologies have become non-negotiable for any organisation that's serious about security.
Endpoint Detection and Response (EDR)
Your endpoints – every laptop, server, and mobile phone – are prime targets for malware and ransomware. Traditional antivirus software just doesn't cut it anymore. EDR solutions provide continuous monitoring of these devices, using behavioural analysis to spot suspicious activity that signals an attack in progress. If a threat is detected, an EDR tool can automatically isolate the infected device to stop the attack from spreading across your network.
Secure Email Gateways
With phishing still being one of the top attack methods, protecting your main communication channel is absolutely vital. A secure email gateway acts as a guard, sitting between the internet and your email server to scan every single message. It filters out spam, phishing scams, and attachments loaded with malware before they ever land in an employee's inbox. This drastically reduces the risk of one wrong click leading to a major breach.
This proactive approach is fast becoming standard practice, especially for businesses in complex digital environments. For instance, Caribbean businesses now treat penetration testing as essential, driven by the risks of rapid cloud adoption and a spike in ransomware attacks. This has led to a shift from occasional tests to a continuous, strategic process that covers networks, cloud services, and APIs.
This forward-thinking mindset is a must for any modern business. For organisations looking to align their tools and strategies with industry regulations, exploring cybersecurity compliance consulting can provide a clear roadmap to achieving a robust and compliant security posture.
Common Questions About Business Cyber Security
When it comes to cyber security, it's easy to get lost in the technical jargon. Business leaders are often left wondering where to even begin, let alone where to invest their time and money. Let's cut through the noise and tackle some of the most common questions we hear from clients.
Think of this as the practical side of the coin, moving from theory to action with clear answers that will help you protect your business.
My Business is Small. Am I Really a Target?
Yes, absolutely. It's one of the most dangerous myths in business today. Attackers often see small businesses as the path of least resistance because they typically have fewer security resources than big corporations.
Consider this: a recent study found that while 87% of small businesses are worried about cyber threats, a staggering 64% still don't think they're an appealing target. That gap in perception is exactly what criminals exploit. You could be a target for your customer data, your financial details, or even a weak link to attack a larger partner in your supply chain. For a small business, a solid security foundation isn't a luxury; it's essential for survival.
Where Should I Start If My Budget Is Limited?
If you're working with a tight budget, the trick is to start with the fundamentals, the high-impact, low-cost steps that give you the most bang for your buck. You don't need a massive investment to make a huge difference in your security.
Employee Training: Your team is your first line of defence. Start by training everyone to spot phishing emails and use strong, unique passwords. Since human error is still a leading cause of breaches, an alert team is one of your most powerful assets.
Multi-Factor Authentication (MFA): Turn on MFA for every critical account you have, from your email to your online banking. It's widely considered one of the single most effective security measures you can implement.
Data Backups: Make sure you have a reliable system for backing up your data and, just as importantly, a plan to restore it. In the face of a ransomware attack, the ability to get your data back quickly is your best lifeline.
What Is the Difference Between Antivirus and a Full Security Solution?
This is a fantastic question, and the distinction is crucial. Think of it like this: an antivirus program is like a good lock on your front door. A full security solution is the entire security system for your building, including locks, an alarm, cameras, and a security guard.
An antivirus program is just one tool designed to spot and remove known malware from a computer. A complete cyber security solution is a multi-layered strategy that protects your entire organisation from a wide range of threats.
A full solution will certainly include antivirus software, but it also brings in a firewall to control network traffic, email filtering to catch phishing scams, regular employee training, and clear policies on how to handle data and respond when something goes wrong.
How Often Should We Review Our Cyber Security Plan?
Your cyber security plan can't be a document that just gathers dust on a shelf. It has to be a living, breathing strategy because the threats you face are constantly changing.
As a rule of thumb, you should conduct a comprehensive review at least once a year. Beyond that, you need to revisit it any time your business goes through a major change. This could be anything from adopting a new software platform or hiring a large group of new people to shifting to a remote-first work model. We also highly recommend running vulnerability scans more frequently; quarterly is a good cadence to catch new risks as they appear.
At Cleffex Digital Ltd, we know that a strong security foundation is the bedrock of business growth. We help organisations navigate their toughest challenges with innovative technology and expert guidance. Discover how our software development solutions can secure and scale your business.







