Secure healthcare software development isn't just a technical checklist; it's a philosophy. It means building medical software where security is woven into the very fabric of the design, not bolted on as an afterthought. This approach integrates robust protections at every single stage of the development lifecycle to shield sensitive patient data, nail regulatory compliance, and keep systems running smoothly in the face of cyber threats. In modern healthcare, this is simply non-negotiable.
The Critical Need for Secure Healthcare Software

In our connected world, patient data has become a goldmine for cybercriminals. Protected Health Information (PHI): things like names, diagnoses, and insurance details are often more valuable on the black market than credit card numbers. This reality puts a massive target on the backs of healthcare organisations.
When a security breach happens, the fallout is devastating and goes far beyond just losing data. An attack can bring patient care to a grinding halt, shatter patient trust, and trigger massive regulatory fines. That's why a security-by-design approach isn't a "nice-to-have" anymore; it's the absolute foundation of patient safety and organisational survival.
The Modern Threat Landscape
The threats we face today are persistent and always changing. Hospitals, clinics, and even small practices are constantly fending off attacks from all angles. In the Canadian healthcare sector, for instance, ransomware attacks have skyrocketed. One major incident targeting one of the country's largest healthcare networks crippled operations, forcing the postponement of surgeries and disrupting patient care.
In response, new legislation now requires AI oversight and risk management in public sectors, including hospitals, which adds even more pressure to get software security right. It's a complex environment, and understanding how to keep up is crucial.
Security isn't just a feature you add to healthcare software. It's the fundamental framework that ensures patient safety, upholds provider integrity, and maintains the trust upon which the entire healthcare ecosystem is built.
To get a handle on this, it's worth exploring how organisations are navigating cybersecurity challenges in the healthcare sector, as the problems of protecting data and meeting regulations are universal.
Why Security Is a Business Strategy
Thinking of secure healthcare software development as just an IT problem is a huge mistake. It's a core business strategy that directly affects your organisation's reputation and long-term viability. Taking a proactive stance on security does more than just prevent financial loss; it builds a bedrock of trust with patients and partners. You can dive deeper into the importance of cybersecurity in the healthcare industry in our related article.
Before we get into the "how," let's look at the "why." Below are the core pillars that secure software is built upon.
Core Pillars of Secure Healthcare Software
This table breaks down the fundamental principles that should guide every decision in healthcare software development.
| Pillar | Description | Why It Matters for Healthcare |
|---|---|---|
| Confidentiality | Ensuring that sensitive PHI is accessible only to authorised individuals. | Prevents data breaches and protects patient privacy, which is a legal and ethical mandate. |
| Integrity | Maintaining the accuracy and completeness of patient data throughout its lifecycle. | Guarantees that clinical decisions are based on correct information, directly impacting patient safety. |
| Availability | Making sure that systems and data are accessible to clinicians when they need them. | Prevents disruptions in care delivery. Downtime in healthcare isn't an inconvenience; it can be life-threatening. |
These three pillars: Confidentiality, Integrity, and Availability, form the classic "CIA Triad" of information security, and they are especially critical in a healthcare context.
A solid commitment to security brings clear business advantages:
Enhanced Patient Trust: When patients feel their information is safe, they're more willing to use digital health tools and engage with their care providers.
Operational Resilience: Secure systems are tough systems. They resist downtime, ensuring clinicians always have the information they need to care for patients without interruption.
Regulatory Compliance: Building security in from the start makes it much easier to meet the strict demands of laws like PIPEDA, helping you avoid crippling fines and legal headaches.
Navigating Canadian Healthcare Compliance and Regulations
Building secure healthcare software in Canada isn't just about writing good code; it's about following a strict set of rules, much like a contractor has to follow a building code. These regulations are the mandatory blueprint for creating a safe, legal, and trustworthy system. Trying to skip them is like building a hospital on a shaky foundation; it’s not a matter of if things will go wrong, but when.
The Canadian regulatory scene is a patchwork of federal and provincial laws, all designed to protect our most sensitive personal information. The big one at the federal level is the Personal Information Protection and Electronic Documents Act (PIPEDA). This law sets the ground rules for how private-sector companies can collect, use, and share personal information during their business activities.
For any healthcare app or platform, PIPEDA provides the baseline for privacy and security. But here’s the tricky part: many provinces have their own health-specific privacy laws that are considered "substantially similar" to PIPEDA. Where these exist, they take precedence, creating a complex but manageable web of rules your team absolutely has to understand.
Understanding Key Federal and Provincial Laws
To get it right, you need a firm grip on the most important pieces of legislation. While PIPEDA is the national standard, provincial acts often lay down more granular, specific requirements for handling personal health information (PHI).
You can find the official guidance on PIPEDA directly from the Office of the Privacy Commissioner of Canada.
This guidance is built around ten fair information principles, which are essentially the golden rules for data protection in Canada. These principles aren't just legal theory; they have a direct impact on your software's design. They dictate everything from how you ask for a patient's consent to the specific security safeguards you need to build in. For any team working on secure healthcare software development, treating these principles as a core part of your design philosophy is non-negotiable.
Here are a few of the most important provincial laws you'll need to know:
Ontario's Personal Health Information Protection Act (PHIPA): This is one of the most detailed health privacy laws in the country. It sets very strict rules for how "health information custodians" (like doctors, hospitals, and by extension, their software vendors) can handle PHI.
Alberta's Health Information Act (HIA): Much like PHIPA, this act lays out the rules of the road for managing health information in Alberta and clearly defines the responsibilities of custodians.
Quebec's Act respecting the protection of personal information in the private sector: Recently overhauled by Bill 25, Quebec now has some of the toughest privacy laws in North America, with massive fines for getting it wrong.
Think of it this way: PIPEDA is the national highway code, but each province can set its own local speed limits and traffic rules. Your software must always obey the strictest rule that applies, depending on where your users are.
Core Compliance Requirements for Your Software
Knowing the names of the laws is one thing, but your development team needs to turn that legal-speak into actual software features and architectural choices. That legal jargon has to become a practical, day-to-day checklist for your developers.
Three of the most critical areas you need to nail are:
Data Residency: This is a big one. Many provincial laws, especially in places like British Columbia and Nova Scotia, require that personal health information stay inside Canada. That means your cloud infrastructure and data storage solutions must be set up to guarantee data never leaves our borders.
Consent Management: Your software has to get clear, explicit consent from patients before it collects or does anything with their data. We're not talking about a tiny checkbox buried in a 50-page terms and conditions document. It has to be easy to understand, and just as importantly, the system must let patients withdraw their consent just as easily.
Breach Notification: If the worst happens and you have a data breach, you are legally required to report it. PIPEDA mandates that you report to the Privacy Commissioner of Canada and tell any affected individuals if the breach poses a "real risk of significant harm." This means your software needs powerful logging and auditing tools to spot and investigate breaches the moment they happen.
As technology marches on, the regulations are evolving right alongside it. The growth of artificial intelligence in medical software is a perfect example. New rules are emerging that will demand more transparency in how AI algorithms work and require rigorous testing to make sure they're not biased. To dig deeper, check out our guide on the challenges and opportunities of AI in healthcare and data privacy in Canada.
Building your solutions on a compliant foundation from day one isn't just about avoiding fines; it's about avoiding incredibly expensive and painful redesigns down the road.
Weaving Security into Your Development Lifecycle
For too long, software development has treated security like a final inspection on a car assembly line. Imagine building an entire vehicle, painting it, and adding the fancy leather seats, only to check if the brakes work right before it rolls off the floor. Finding a major flaw at that stage isn't just a setback; it's a disaster that often requires a costly, time-consuming teardown. In healthcare, that reactive approach is a risk no one can afford to take.
The smarter, modern way is to build security in from the very beginning. This is the core idea behind the Secure Software Development Lifecycle (SSDLC). It's a fundamental shift in thinking where security isn't a final hurdle to clear but a continuous thread woven through every phase, from the first brainstorm to post-launch support. This is often called the shift left security approach; you're moving security activities earlier (or "left") in the project timeline.
This cultural shift is brought to life through DevSecOps, a practice that breaks down the traditional walls between development, security, and operations teams. Instead of passing work from one silo to another, everyone collaborates to build, test, and release software that is secure by its very nature. The goal is straightforward: make security everyone’s job, all the time.
The flowchart below gives you a sense of the compliance landscape that shapes a secure development process here in Canada, layering federal laws with provincial rules and even new considerations for AI.
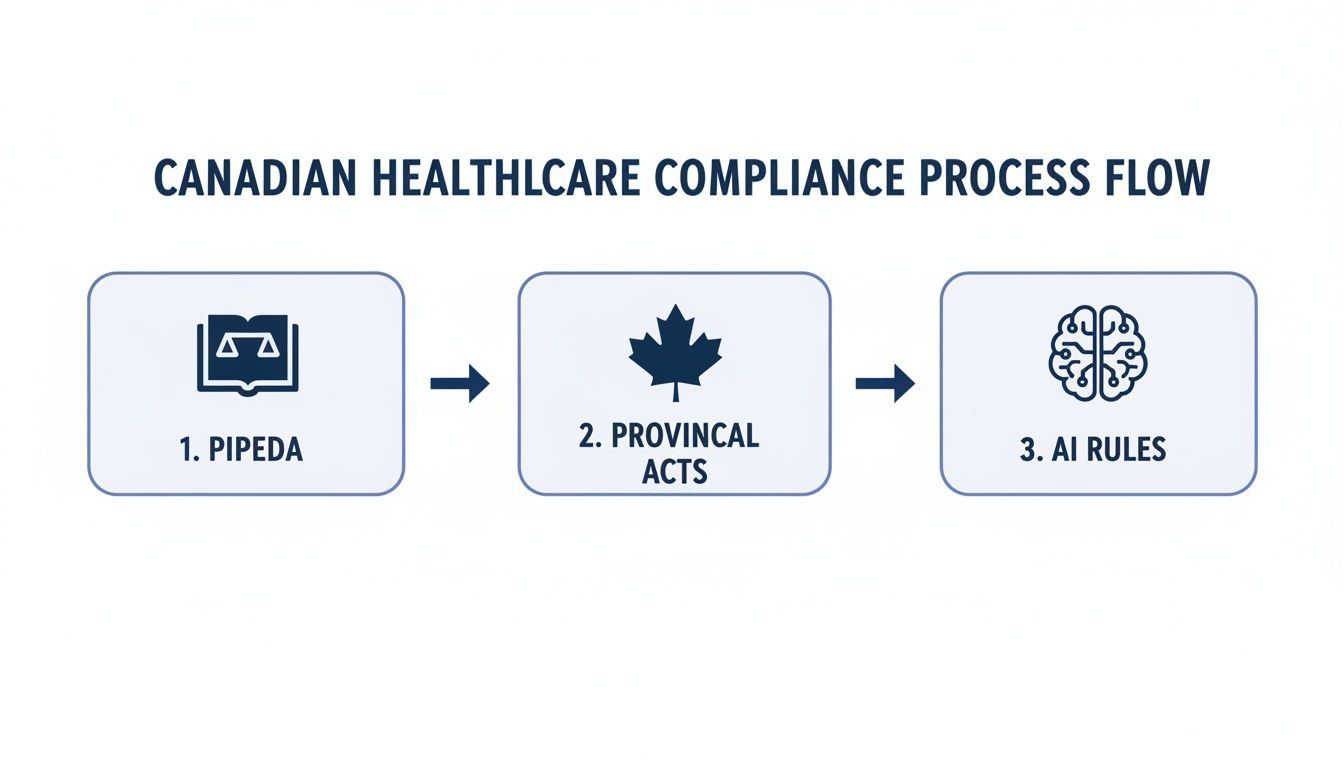
As you can see, building secure healthcare software means navigating multiple layers of rules, starting with broad federal standards like PIPEDA and then drilling down into more specific provincial and technology-focused guidelines.
Integrating Security at Every Stage
A great SSDLC isn't about piling on more work. It’s about working smarter by catching security weaknesses early, when they're far simpler and cheaper to fix. Let's walk through what this looks like in the real world.
1. Planning and Requirements: Security starts before a single line of code gets written. This is where the team performs threat modelling – a structured exercise to think like an attacker and anticipate potential weak points. These insights directly inform the security requirements that are built into the project plan from day one.
2. Design and Architecture: With a clear picture of the threats, architects can design defences right into the software’s blueprint. This means planning for strong encryption, foolproof authentication methods, and strict role-based access controls to ensure no one has more access than they absolutely need.
3. Development and Coding: Developers follow secure coding standards to sidestep common vulnerabilities like SQL injection or cross-site scripting. Automated tools are plugged directly into their coding environment, giving them real-time feedback on potential security issues as they type.
4. Testing and QA: The intensity of security testing really picks up here. A mix of automated scans and hands-on manual reviews is used to hunt for any flaws that might have slipped through. This phase is all about making sure the security controls designed earlier actually work as intended.
5. Deployment and Release: Before flipping the switch, a final security review ensures the live environment is locked down. This often includes penetration testing, where ethical hackers are hired to try to break into the system to expose any lingering vulnerabilities.
6. Maintenance and Monitoring: Security doesn’t end at launch. It’s a constant process. The team must continuously monitor the application for any unusual activity, apply security patches the moment they're available, and have a clear incident response plan ready to go.
The Tools and Culture of DevSecOps
DevSecOps hinges on smart automation to make security a seamless part of the development workflow. By integrating security tools directly into the CI/CD (Continuous Integration/Continuous Deployment) pipeline, developers get instant feedback. They can fix a vulnerability in minutes, not weeks after it was introduced.
In a true DevSecOps culture, security isn't seen as a roadblock to innovation. Instead, it becomes an enabler of quality, allowing teams to ship new features faster and with far more confidence.
Getting this right has never been more critical. The Canada Healthcare Cybersecurity Market is forecasted to reach USD 11.82 billion by 2035, a massive figure fuelled by a rise in cyberattacks and the widespread move to digital health. With 92% of Canadian healthcare organisations hit by attacks recently and Electronic Health Record (EHR) adoption now at 62%, the need for these deeply integrated security practices is undeniable.
Integrating DevSecOps means embedding specific security activities and tools into each phase of the development lifecycle. Here’s a quick look at how that breaks down.
DevSecOps Practices Across the SDLC
| SDLC Phase | Key DevSecOps Activity | Example Tools |
|---|---|---|
| Planning | Threat Modelling & Security Requirements | OWASP Threat Dragon, Microsoft Threat Modeling Tool |
| Coding | Real-time Code Scanning & Secure Coding Training | SonarLint, Snyk Code |
| Building | Static Application Security Testing (SAST) | Checkmarx, Veracode |
| Testing | Dynamic Application Security Testing (DAST) | OWASP ZAP, Burp Suite |
| Releasing | Software Composition Analysis (SCA) | Snyk Open Source, Dependabot |
| Deploying | Infrastructure as Code (IaC) Scanning & Pen Testing | Checkov, Metasploit |
| Operating | Continuous Monitoring & Incident Response | Splunk, Datadog |
By adopting this structured approach, you ensure security is never just a "check-the-box" activity but a continuous, automated, and collaborative effort that protects your application from the inside out. This isn't just about compliance; it's about building trust and resilience in a world where patient data is more valuable and more vulnerable than ever.
Architectural Patterns for Protecting Patient Data
Think of your software's architecture as the blueprint for a high-security vault. You wouldn't design a bank with flimsy walls and a single lock on the door. In the same way, building secure healthcare software means embedding security into its very foundation, not just adding it as an afterthought. These architectural patterns are the reinforced walls, the multi-lock doors, and the surveillance systems that protect your most valuable asset: Protected Health Information (PHI).
When you build security into the design from day one, you create a system where protecting patient data is the default, not the exception. This isn't just about compliance; it's about building a trustworthy solution that patients and providers can rely on.
Sealing Data with Encryption
The absolute bedrock of any secure healthcare application is rock-solid encryption. It's like sealing every single piece of patient data inside its own tamper-proof digital envelope. This protection isn't optional, and it needs to be applied in two critical scenarios:
Encryption at Rest: This is for data that’s just sitting there, stored in your databases, on servers, or in backups. If someone manages to walk out with a hard drive or gain unauthorised access to your database, the data is nothing but unreadable gibberish without the decryption key.
Encryption in Transit: This protects data while it’s on the move. Think of the journey from a patient’s smartphone app to your cloud server, or even between your own internal services. This security layer prevents anyone from "eavesdropping" and snooping on the data as it travels across the network.
When it comes to the encryption itself, using strong, industry-standard algorithms like AES-256 is the non-negotiable minimum. Anything weaker is like trying to secure a fortress with a bicycle lock.
Controlling Access with Authentication and Authorisation
With all your data securely encrypted, the next question is: who gets the keys? That’s where authentication and authorisation come in, working together like a bank's meticulous security checkpoint system.
Authentication is all about verifying identity – proving someone is who they say they are. In today's world, a simple username and password just don't cut it anymore. The standard is now Multi-Factor Authentication (MFA), which demands a second piece of proof, like a code from a mobile app or a fingerprint scan. It’s the difference between asking "What do you know?" and "What do you know, and what do you have?"
Authorisation, on the other hand, kicks in after someone has been authenticated. It dictates exactly what that user is allowed to see and do. This is governed by the Principle of Least Privilege, a simple but powerful idea: give people access only to the information and tools they absolutely need to do their jobs, and nothing more.
A well-designed access control model ensures a surgeon can pull up a patient's vitals but can't touch billing records. Likewise, an administrator can schedule appointments but has no business viewing sensitive clinical notes. This is the heart of Role-Based Access Control (RBAC).
Implementing a robust RBAC system is crucial. It lets you define clear roles, like ‘nurse,’ ‘doctor,’ or ‘billing specialist’, each with a specific set of permissions. This drastically cuts down on the risk of both accidental data leaks and malicious insider activity.
Containing Threats with Network Segmentation
Even with the most robust defences in place, you have to assume that a breach is possible. That’s the mindset behind network segmentation. The best analogy is a modern ship built with multiple watertight compartments. If one section is breached and starts taking on water, the sealed compartments stop the entire vessel from sinking.
In your software architecture, segmentation works by isolating different parts of your network from each other. For example:
The database holding all the sensitive PHI lives in its own heavily fortified, isolated segment.
Your public-facing web servers sit in a separate, less-trusted segment.
Internal tools used by your administrative team are in yet another segment.
Firewalls with very strict rules act as the bulkheads between these segments, only allowing pre-approved and tightly controlled communication to pass through. If an attacker manages to compromise a public web server, segmentation prevents them from moving sideways into the network to get to the crown jewels – the patient data. This containment strategy is a cornerstone of secure healthcare software development, ensuring that a single failure doesn't lead to a catastrophic system-wide breach.
A Practical Guide to Security Testing and Validation
Building a secure architectural foundation is a fantastic start, but it’s only half the battle. Now comes the hard part: rigorously testing and validating every defence you’ve built. This is the phase of secure healthcare software development where you prove your application can actually stand up to real-world attacks. It’s where theoretical security meets practical, robust protection.
Think of it like building a bank vault. You can have the most brilliant blueprint in the world, but you still need to stress-test it. You have to confirm the walls are as strong as designed, the locks can't be picked, and the alarms work perfectly. This is exactly what a multi-layered testing approach does for your software; it provides the comprehensive assurance that you're ready to protect sensitive patient data.
Thinking Like an Attacker with Threat Modelling
The best defence often begins with a great offence. Threat modelling is a proactive security exercise where your team deliberately puts on their "black hat" and thinks like an attacker. It's a structured brainstorm that happens long before a single line of code is written, forcing you to answer some tough questions:
What are our most valuable assets? (e.g., patient records, billing information)
Who would want to attack our system and why?
Where are the potential weak spots in our proposed design?
How could an attacker actually exploit those weaknesses?
By mapping out these potential threats and attack vectors early on, you can build the countermeasures right into the architecture from day one. This is always more effective and far less expensive than trying to patch security holes after the fact.
SAST vs. DAST: The Blueprint and Building Inspection
Once development kicks off, automated testing is your best friend for catching vulnerabilities early and often. Two core methods for this are Static and Dynamic testing, and they work in very different ways.
Imagine you're constructing a new hospital wing. Static Application Security Testing (SAST) is like having an inspector meticulously review the architectural blueprints before any construction begins. They’re looking for structural flaws, unsafe material specifications, or design errors. In the same way, SAST tools scan your application's source code without even running it, hunting for common coding mistakes and security flaws like SQL injection vulnerabilities or improper data handling.
SAST gives you an "inside-out" view, identifying potential issues right at the source. It's an indispensable part of a secure development lifecycle because it catches bugs when they are cheapest and easiest to fix.
On the other hand, Dynamic Application Security Testing (DAST) is like testing the completed hospital wing's security systems in a real-world scenario. This inspector doesn't care about the blueprints; they’re actively trying to pick the locks, bypass the security cameras, and test the fire alarms. DAST tools do the same to your live application, attacking it from the outside just as a real hacker would to find exploitable vulnerabilities. For a deeper look at this process, especially for interconnected systems, you can learn more about comprehensive API security testing strategies.
Validating Defences with Penetration Testing
The final, and arguably most critical, validation step is penetration testing, often shortened to "pen testing." This is where you bring in the experts, a team of certified ethical hackers, to conduct a controlled, authorised attack on your system. Their sole mission is to find and exploit any vulnerabilities that your internal teams and automated tools might have missed.
A proper penetration test simulates a genuine cyberattack, giving you invaluable, real-world insight into how your application holds up under pressure. It's the ultimate reality check that takes your security from theory to proven fact. A clean report from a reputable pen testing firm gives everyone involved, from executives to regulators, the confidence that your software is truly secure and ready to safeguard patient trust.
Maintaining Security After Launch

Getting your healthcare software launched is a huge win, but it’s really just the starting line for security, not the finish. The moment your application goes live and starts handling real patient data, it’s exposed to a world of constantly changing threats. True secure healthcare software development means accepting that security isn't a one-and-done task; it’s a process of constant vigilance.
Think of it like the security system in a hospital. You wouldn't just install cameras and alarms and then walk away. Real security means having someone actively watching the monitors, ready to respond the second something seems off. This is precisely the mindset needed for managing your software after launch.
The Importance of Continuous Monitoring
Continuous monitoring is all about keeping a constant, watchful eye on your application and its environment to catch security threats as they happen. It’s your round-the-clock digital security guard, scanning for suspicious activity, failed login attempts, or strange data movements that could hint at a breach. Without it, you’re flying blind.
This isn’t about a person staring at a screen 24/7. It involves using a set of automated tools that give you a clear, real-time picture of your system's health and security. The core activities here include:
Log Management: This means collecting and reviewing the activity logs from every part of your system: servers, databases, firewalls, to piece together a complete story of who did what, and when.
Intrusion Detection Systems (IDS): Think of these as digital tripwires. They’re programmed to spot known attack patterns or policy violations and sound the alarm immediately.
Vulnerability Scanning: Your live application and its infrastructure are regularly scanned for new weaknesses that hackers have discovered, giving you a chance to patch them before they can be exploited.
This constant watchfulness shifts your team from a reactive mode (cleaning up a mess) to a proactive one, where you can neutralise threats before they become full-blown disasters.
An effective monitoring strategy doesn’t just tell you what happened yesterday. It gives you the early warnings you need to stop a minor issue from turning into a headline-making data breach. It transforms raw data into real security intelligence.
Preparing for the Worst With an Incident Response Plan
Even with the best defences, you have to assume that a security incident could still happen. An Incident Response (IR) Plan is your pre-written playbook for what to do when that alarm goes off. It’s the digital equivalent of a hospital’s fire drill – a practised, step-by-step procedure ensuring everyone knows their role and can act quickly and correctly under pressure.
Having a solid IR plan is crucial for limiting the damage, getting services back online fast, and meeting your legal obligations for breach notification under regulations like PIPEDA. It brings order to a potentially chaotic situation, which helps preserve patient trust and keep the business running. A good plan will clearly outline every phase of the response, from the initial detection and analysis through to containment, removal, and recovery.
Frequently Asked Questions
When it comes to building secure healthcare software, balancing innovation, budgets, and regulations can feel like a tightrope walk. It's only natural to have questions. Here are some of the most common ones we hear, along with some straightforward answers.
How Can a Small Clinic Afford Secure Software Development?
For a smaller clinic, it’s not about having a massive security team; it's about being strategic. You can make a huge difference by focusing on foundational security measures that give you the most bang for your buck.
Start by choosing established, PIPEDA-compliant vendors for any software you buy off the shelf. Then, make Multi-Factor Authentication (MFA) non-negotiable for every system, and get your staff into a routine of regular security awareness training. If you’re developing a custom tool, you don't need to hire a full-time expert; consider bringing in a specialised firm on a project basis. Thinking in terms of risk and focusing on protecting your most sensitive data first is always the most cost-effective way forward.
What Is the Most Important Security Practice for a Startup?
If you're a healthcare startup, the single most critical thing you can do is bake security into your product from the very beginning. Embracing a "shift-left" or DevSecOps mindset means security isn't a final checkbox; it's a fundamental part of your architecture and code from day one.
This really comes down to a few key actions:
Run threat modelling exercises early in the design phase to spot potential weaknesses before a single line of code is written.
Integrate automated security testing tools right into your development pipeline so they run continuously.
Foster a culture where every developer takes ownership of writing secure code.
It's far easier and cheaper to build security into your DNA from the start than to go back and patch deep, structural vulnerabilities after you've already launched.
It's a common misconception, but using a major cloud provider doesn't automatically make your application compliant. They are responsible for the security of the cloud, but you are entirely responsible for securing everything you build and run in the cloud, from your application code to your data configurations.
How Do I Improve Security for an Existing Healthcare App?
The best way to start is by getting an honest assessment of your current situation. A thorough security audit combined with a professional penetration test will cut through the guesswork and show you exactly where your biggest risks are.
With those results in hand, you can build a sensible roadmap for improvements. You'll likely find some "low-hanging fruit" that can make an immediate impact, like enforcing MFA everywhere, updating outdated software libraries (patch management), and tightening user access controls to follow a "least privilege" model. Alongside these technical fixes, start ongoing security training for everyone. Human error is still one of the most common ways attackers get in, so a combination of technical safeguards and human awareness is your strongest defence.
At Cleffex Digital Ltd, we specialise in building secure, compliant, and high-performing software solutions that help healthcare organisations protect patient data and drive better outcomes. Contact us to learn how we can strengthen your development process.








